November 6, 2023 ↩
Switches vs Routers
Both are store-and-forward.
Routers: network-layer devices (examines network-layer headers).Switches: link-layer devices (examine link-layer headers).
Both have forwarding tables.
Routers: Compute tables using routing algorithms, IP addresses.Switches: learn forwarding table using flooding, learning, MAC addresses.
Flooding is a non-adaptive routing technique following this simple method: when a data packet arrives at a router, it is sent to all the outgoing links except the one it has arrived on.
ARP Poisoning is a type of attack, where if Host A wants to send message to Host B, it passes through Host C and the router.
Virtual LANs (VLANs)
Q: What happens as LAN sizes scale, users change point of attachment?
Virtual LANs enable networking between different points of network without the use of router, and instead uses a switch.
Single Broadcast domain
- Scaling : all layer-2 broadcast traffic (ARP,DHCP,unknown MAC), must cross entire LAN.
- Efficiency, security, privacy, efficiency issues.
Administrative Issues
- User moves across physically, but wants to remain logically attached to initial network.
Port-based VLAN
Switch ports grouped so that single physical switch operates as multiple virtual switches. Operates in the physical layer, not the transport layer. It has 16 ports.
Traffic Isolation: Frames to/from ports 1-8 can only reach ports 1-8.- Ports can be dynamically assigned among VLANs.
Forwarding between VLANSis done via routing (just as with separate switches).
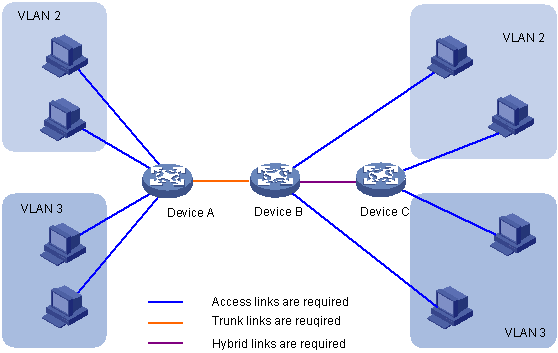
VLANS spanning multiple switches
Trunk port carries frames between VLANS defined over multiple physical switches.
- Frames forwarded within VLANs b/w switches must carry VLAN ID info.
- 802.1q protcol adds/removes additional header fields for frames forwarded between trunk ports.
EVPN - Ethernet VPNs (aka VXLANs)
IP networking between say Sunnyvale data center and Banglore data center, to send ethernet packet. 2 interfaces which connected to individual switch port.
Layer-2 Ethernet switches logically connected to each other (using IP as an underlay)
Install tor broswer. Uses VPN to enter darknet. Onions? Curiosity killed the cat. But sir says be curious. Lol
In an onion network, messages are encapsulated in layers of encryption, analogous to the layers of an onion. The encrypted data is transmitted through a series of network nodes called “onion routers,” each of which “peels” away a single layer, revealing the data’s next destination.

